Self Sovereign Identity: A distant dream?
Who are you? And who decides your trustworthy existence? The answer, the systems involved differ in the real and virtual world. To eradicate these differences, blockchain can possibly provide a much authorized way of establishing identity which could eventually be used to gain trust of the services we shall avail.
Nowadays when you register for a service, say you sign up on Facebook, it’s quite likely that it can be compromised if someone intends to. Identity fraud comes in here. It is basically the use of a person’s personal information by someone else without his/her permission. Most identity fraud is committed in the context of financial advantage, such as accessing a victim’s credit card and bank accounts. Identity theft has reached epidemic levels in the UK, with incidents of this type of fraud running at almost 500 a day. During the first six months of 2018 there were a record 89,000 cases of identity fraud, which typically involved criminals pretending to be an individual in order to steal their money, buy items or issue a loan or car insurance in their name. Therefore, one important question arises. Is it possible to use different services being provided to a customer with a surety that our identity will never be compromised? Voilà! Blockchain comes to the rescue!
This blog is more technically oriented since I will describe how this idea was implemented using various libraries, cryptographic modules and web frameworks (Django in my case). I am assuming that you’re familiar with the concept of blockchain, if not, you may use this link as reference: https://anders.com/blockchain/. Since the record of services we use cannot be decentralized, the copies of blockchain will only be with the user, service provider and trusted authority on which the usage of service will be stored(called transactions). Okay, lot’s of technical terms here. Putting this into simpler words, how can one ensure that verified identity used to make this transaction isn’t shared with the service provider? This question is answered through a basic web application, my team-mate (Aman Sharma) and I ideated and developed during a hackathon.
Every individual is assigned a digital wallet(fancy term for a directory on your PC or handheld device which stores all his/her verified documents) by a trusted authority assuming there is only one(preferably government) which issues these ID’s and contains all the important documents that can be accessed by that individual in the time he requires a service. Also every single document of the person is digitally signed with his own self-generated public and private key along with hashing algorithm that generates a valid and verified message signature corresponding to that document. This message signature ensures his/her information is verified and best part is that one cannot trace back the individual’s identity since the signature is hashed. One can access his digital wallet with a login ID and password kept solely with the individual.
Now let’s dive deeper into the intricacies of the problem which is solved by our application. Earlier we had to trust a service provider with our identity as the service needed to use it for providing us with the service. Although any good service would take your permission to use this data but let’s face it, your data cannot have a mere usage as training set for a machine learning model because it’s your data and it’s meant to be private. Now, what if there was a solution to this problem too. So our proposition is that the individual can access a service by a QR code displayed by the service provider. Now the QR code will redirect to the only other trusted authority(which has been the government since the starting of the blog) verified page which will ask you to fill in the only one single field per document required which is the verified message signature for that document that is kept secretly with you in your wallet and in the database maintained by that trusted authority. After all the message signatures are verified, we can access that service easily. Since the data we entered was on the trusted authority’s page, the service provider can never really know your identity but still they know it’s verified. Shopping has never been so easy :)
Okay now you got access to the service, your data is not passed on to the service provider but still job’s not complete. What if the service provider refuses to accept that the transaction never happened in the past or user tries to deny the service’s usage. Yeah, daddy’s still got work. Which is why everything from start was about blockchain only. The transactions are stored in three different copies of the blockchain. with the user, service provider and with the trusted one. I am reiterating this point because this distribution of blockchain forms the whole crux of secure transactions. In simpler words, it will follow the 51% attack rule and prevent tampering of transaction by mining.
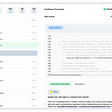
The same JSON response(this blockchain) will be maintained for a particular service with all the parties. Port 5001 hosts the blockchain for user. Similarly port 5002 and 5003 host the same blockchain for service provider and the trusted authority.
Although the idea is brilliant, but its practical usage has a drawback too. Mining cost of a block has always been a huge financial issue. This will require a lot expenditure on the user’s side to access a service so that a transaction can be saved. But still, it can have a great potential if given a thought like we did in a college level hackathon.
Happy brainstorming!